Security and SiEM for IBM i STR-iCT
STR-iCT: a security application dedicated to IBM i With decades of experience in securing IBM i systems, and the auditing of hundreds of partitions, I.GAYTE.IT has created the software package dedicated to securing IBM i systems: STR-iCT
Security and SiEM
for IBM i/AS400
Introduction
IBM i (formerly AS/400) are mission-critical systems, often handling the majority of a company's activities. The security of IBM i (formerly AS/400) environments is a major challenge for IT Departments.
Thanks to SIEM (Security Information and Event Management) integration, it's possible to detect threats in real time and improve compliance with regulations such as RGPD or PCI DSS.
But standard network security tools ignore or at best misunderstand this system.
In this context, STR-iCT emerges as the tailor-made solution, developed specifically to overcome these shortcomings and offer unrivalled security coverage for IBM i systems.
Why Implement STR-iCT on IBM i/AS 400?
The IBM i (AS/400) system is robust but still vulnerable to cyber threats. A SIEM IBM i solution helps to:
✅ Centralize security logs.
✅ Detect suspicious activities in real-time.
✅ Ensure compliance with ISO 27001, GDPR, and PCI DSS regulations.
At the heart of IBM i security
How Does a SIEM Work on AS400?
A SIEM AS400 collects and analyzes logs from the IBM i operating system. It identifies unauthorized access, sensitive file modifications, and intrusion attempts.
On IBM i a SIEM is essential for an effective cybersecurity strategy. Choosing the right solution tailored to your infrastructure will enhance the protection of your AS/400 system.
Comprehensive, intelligent monitoring with STR-iCT
Our STR-iCT software in 3 points
- 1 STR-iCT probes can retrieve all available IBM i events
- 2 A unique expert system assesses the risk level of each of these events based on a number of parameters
- 3 The available data (remote IP address and port, profile used, action taken, risk level, etc.) is exported to a dispatcher responsible for alerting if necessary and sending the data to a data repository, a SiEM, an external SOC, etc.
PDF presentation
Probes : intercept events
Our perfect knowledge of the IBM i and its mechanisms enables us to recover a large number of events linked to security and/or traceability.
Dozens of probes are available and can be configured to collect the data you need.
- Attempted intrusions
- Password errors
- Attempt to access an unauthorized object
- NetServer connection attempt
- Kerberos login (SSO)
- Use of a non-existent / deactivated user profile
- Object deletion
- DST/SST management
- Metric
- IFS access via NetServer
- FTP access
- System security audit
- Track changes to a table column
- Managing system values
- User profile management
- ODBC/JDBC SQL access
- and many more...
Expert System risk definition
Each event is processed by our Expert System to determine the risk it poses to the IBM i and the entire network.
It draws on I.GAYTE.IT's expertise in IBM i security, its experience of attempted intrusions into these systems, and its knowledge of cybersecurity.
SiEM: STR-iCT for IBM i Event Manager
SIEM dedicated to IBM i
STR-iCT can be considered as a true SIEM (Security Information Event Manager) dedicated to the IBM i.
It collects data, assesses risk and triggers alerts.
It can operate as a stand-alone solution for entities that do not already have a SIEM for their network.
Are you SiEM or SIEM?
Those who already have a SIEM to manage the security of all network elements know that the IBM i is generally excluded. STR-iCT can transfer the data to them for centralized management. STR-iCT interfaces with the leading SIEMs on the market, so don't hesitate to contact us. With STR-iCT, you can decide on the type of data transmitted to the SIEM. STR-iCT can be used to archive data (data repositories) in order to reduce the cost of an external SIEM, which is often calculated on the basis of the traffic managed. In this case, only critical (high-risk) information is communicated to the SIEM.
The STR-iCT data well
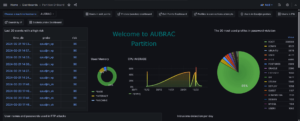
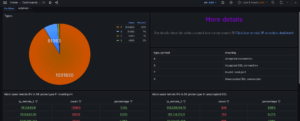
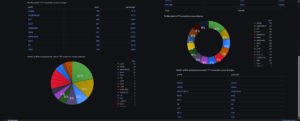
data repository and graphic display

It's a unique place, with a graphical interface that presents you with configurable dashboards, and lets you use an SQL query to meet your every need.
This highly ergonomic interface, based on Grafana, is fully configurable for ease of use.
Traceability
Only traceability allows you to understand past events.
What connections were attempted from which IP address, who modified the transfer file last week, what jobs were started by a profile, who modified system values or SST/DST profiles...?
You can easily retrieve this information from the graphical interface of our data well.
Retention of information for each type of event is simply configurable via our graphical interface.
Long-term retention (cold data) is also available.
External SOC
Some organizations use external SOCs (Security Operation Centers) to manage network security.
STR-iCT communicates important data to these SOCs, so that they have all the IBM i data they need to carry out their mission.
Visual configuration interface
STR-iCT also features a simplified C# interface for configuring the entire software in the form of a heavy-duty application.
In particular, it can be used to configure probes or false positives (IDS).
Move on to the next step
Contact us to discover STR-iCT, our security application dedicated to IBM i