📢 IBM has issued a new security bulletin concerning IBM® SDK Java™ Technology Edition and IBM® Runtime Environment Java™ used by IBM i.
🚨 Two major vulnerabilities have been identified:
✔️ Partial denial of service via Networking & Serialization components [CVE-2024-21208 & CVE-2024-21217]
✔️ String length calculation error in Eclipse OpenJ9 [CVE-2024-10917]
⚠️ Vulnerability details
🔴 CVE-2024-21208 & CVE-2024-21217 – Partial Denial of Service (DoS)
🔹 Impact: An unauthenticated attacker with network access via several protocols can exploit this vulnerability in Java SE.
🔹 How can it be exploited? The flaw affects the Networking and Serialization components, which can compromise the platform by causing a partial denial of service.
🔹 CVSS score: 3.7 / 10
🔴 CVE-2024-10917 – Problem in JNI GetStringUTFLength (Eclipse OpenJ9)
🔹 Impact: In versions lower than 0.47 of Eclipse OpenJ9, the JNI GetStringUTFLength function may return an incorrect value when encapsulated.
🔹 Fixed: Since version 0.48, the value returned is correct, but may be truncated.
🔹 CVSS score: 5.3 / 10
📌 Official source: 🔗 IBM security bulletin
🛠️ How to correct these flaws?
💡 IBM recommends that you immediately apply the appropriate application patches to your IBM i:
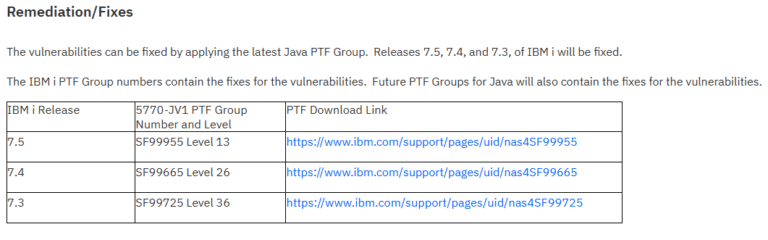
(see attachment 📎)
✔️ Update your Java versions to avoid any risk of exploitation.
✔️ Check your JVM version and make sure it’s at least version 0.48.
⚠️ Don’t delay in applying these patches to strengthen your system’s security!
⚡ Act now to secure your IT environment with STR-iCT!
🔐 Keep up to date with the latest cybersecurity alerts! 🚀